What Is Ping?
What is ping? What does it do, and how does it work?

What is ping? What does it do, and how does it work?

A general overview of the Ping software utility.
A general overview of the ping software utility. Ping is a simple computer network software utility used to test and verify the reachability of a host on an Internet Protocol (IP) network. It works by sending packets from the source to the target host which if it is accessible through the network, then sends packets back. The source host then analyzes the returning packets to determine if the target host is accessible and calculates simple statistics of packets traversing the network.
The ping utility was written by Mike Muuss in December 1983, while he was working at the US Army Research Laboratory. It was named after the sound sonar makes when bouncing off underwater objects. Having said that, as time passed, the name ping was transformed into the acronym that is commonly used today: Packet InterNet Groper or PING. The goal of the utility was to provide a simple way to test IP network connectivity and collect measurements regarding a network. The software utility is classified as public domain -- it has been this way from PING's initial release.
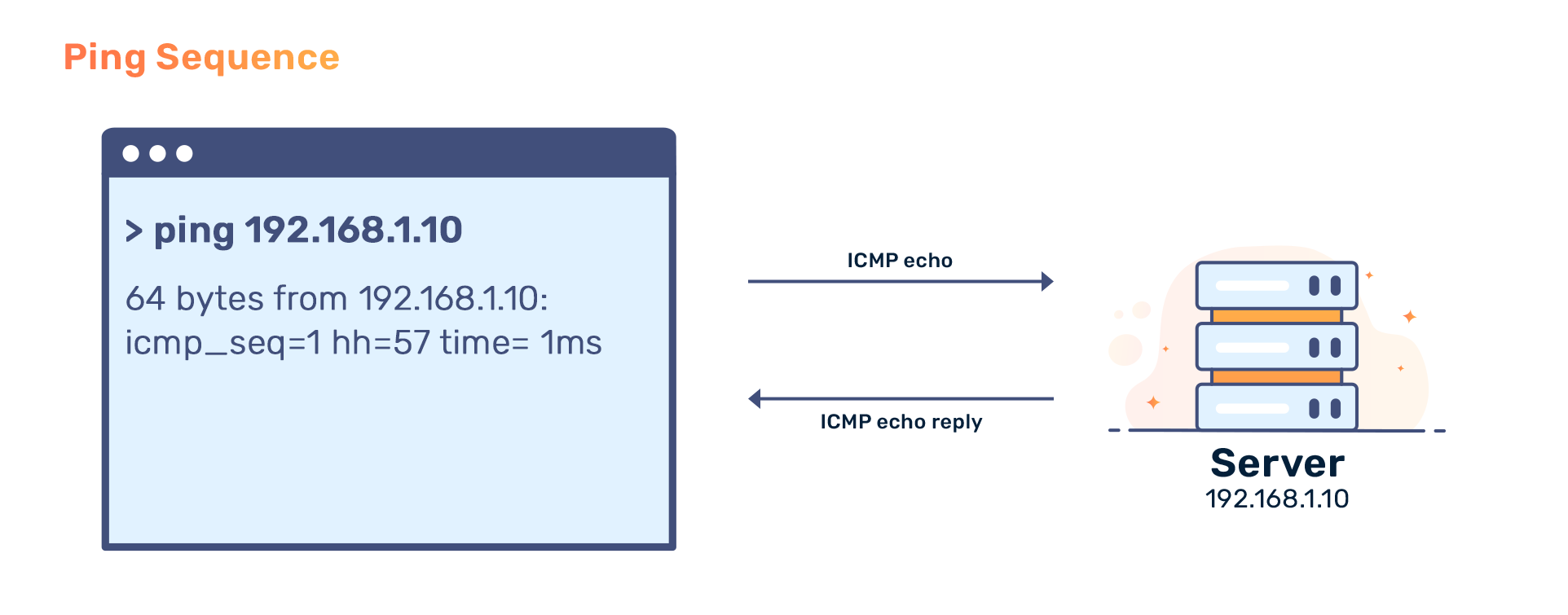
Ping uses the Internet Control Message Protocol (ICMP) packets for its operation. Pinging involves sending an ICMP echo request to the target host and waiting for an ICMP echo reply. The utility reports packet loss, errors and a statistical summary of the results (minimum, maximum, the mean round-trip times and standard deviation of the mean).
There are multiple implementations of the ping utility with additional functionality, such as a controllable payload size, test count, network hop limit (TTL), interval time between requests and time to wait for a response (round-trip time (RTT) or latency). Ping also enables us to record the network route from the source to the target host, which is relayed to the source host via the echo reply message. It also tests Domain Name Service (DNS) name resolution. There are versions of ping that work with Internet Protocol version 6 (IPv6) networks, using ICMPv6.
The following is the output of the ping utility (run on Linux). In the current configuration, 4 packets are sent to the target host. Seen below is a combination of the correct IP being resolved through a DNS resolver, successful ICMP echo reply and completion of a single ping test:
ping -c 4 bunny.net
PING bunny.net (A.B.C.D) 56(84) bytes of data.
64 bytes from A.B.C.D (A.B.C.D): icmp_seq=1 ttl=57 time=1.47 ms
64 bytes from A.B.C.D (A.B.C.D): icmp_seq=2 ttl=57 time=1.50 ms
64 bytes from A.B.C.D (A.B.C.D): icmp_seq=3 ttl=57 time=1.74 ms
64 bytes from A.B.C.D (A.B.C.D): icmp_seq=4 ttl=57 time=1.44 ms
--- bunny.net ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 1.443/1.537/1.744/0.120 ms
The following is the output of running ping, on Linux, for a 4-packet test. Compared to the test above, the destination was unreachable (i.e. no ICMP echo reply was received):
ping -c 4 blackhole.bunny.net
PING bunny.net (E.F.G.H) 56(84) bytes of data.
From E.F.G.H icmp_seq=1 Destination Host Unreachable
From E.F.G.H icmp_seq=2 Destination Host Unreachable
From E.F.G.H icmp_seq=3 Destination Host Unreachable
From E.F.G.H icmp_seq=4 Destination Host Unreachable
--- blackhole.bunny.net ping statistics ---
4 packets transmitted, 0 received, +4 errors, 100% packet loss, time 3000ms
Ping uses IPv4 datagrams or more specifically ICMP packets have the following format:

We have the IPv4 packet header in blue, where ICMP is specified with value 1 in the protocol field and 0 in Type of service. In red, we have the ICMP packet header and payload. In the header, we determine the type of ICMP message, code, the checksum of the ICMP packet and header data.
For an ICMP echo request, the type has a value of 8. For a reply, a value of 0 is given. With ICMP echo requests and replies, the ICMP header comprises of identifier and sequence number. The ICMP payload can be of an arbitrary length determined by the individual implementations. That does not mean that the packet (including the IPv4 and ICMP headers) can exceed the maximum transmission unit or maximum packet size determined by a network (due to a risk of fragmentation among multiple packets).
Unfortunately, like many utilities, ping can be misused for malicious purposes. For example:
The layer of the OSI model that handles communication over networks.
A tool to measure latency on the 3rd layer.