What Are Distributed Denial of Service (DDoS) Attacks?
What are DDoS attacks and how do they disrupt websites and services?

What are DDoS attacks and how do they disrupt websites and services?

Distributed Denial of Service (DDoS) attacks are one of the most powerful ways to disrupt the proper functioning of a web server. The general principle behind most DDoS attacks is the same: to overwhelm a victim’s web server with excessive traffic such that the server machine or its networking infrastructure can't handle the load.
This is analogous to a paper shredding machine. Imagine that the machine is capable of shredding up to five sheets of paper in one go. This machine has been continuously shredding less than five sheets of paper for weeks without a problem. One day, someone deliberately puts a thick stack of sheets (say, 50 pages) into the shredding machine, which far exceeds its shredding capacity. The machine is jammed and can't accept paper for shredding. A DDoS attack works similarly by deliberately clogging up a web server and its infrastructure with traffic that exceeds its maximum capacity.
Sometimes, a web server may be overwhelmed by legitimate traffic (e.g. a popular shopping website carrying out a massive limited-time sale) and shows symptoms similar to a DDoS attack, like extremely slow loading of a website or a complete shutdown of the web server. A real DDoS attack is made up of malicious web traffic that is intentionally sent by an individual or a small group of people to disrupt service.
Distributed Denial of Service (DDoS) attacks are usually carried out by a large network of machines. These machines are usually compromised by malware, allowing someone else to remotely command these machines. Such compromised machines are called zombies or bots, and large networks of such compromised machines are known as botnets.
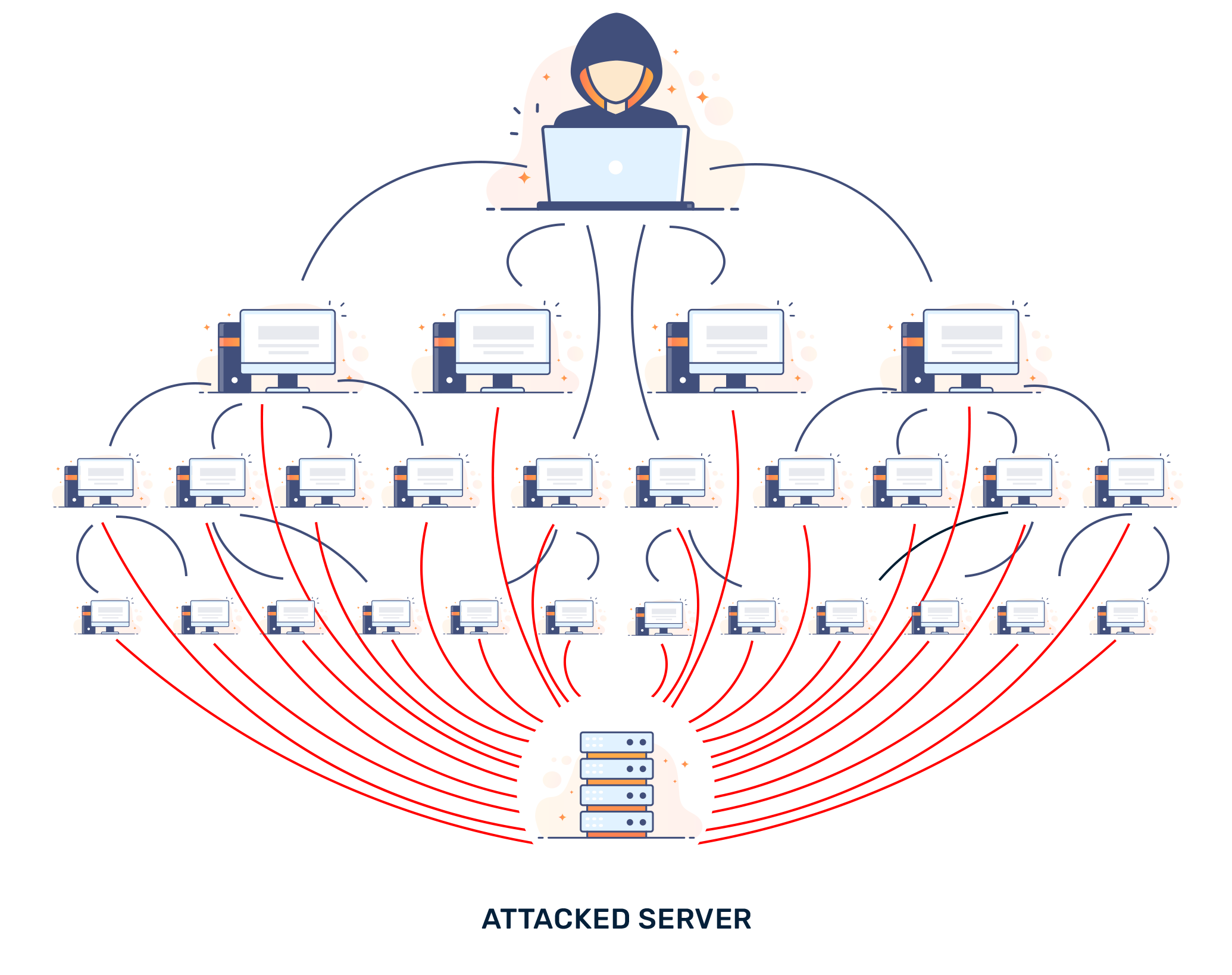
The actual owners of these zombie machines or bots may not know that their machines have been compromised and are part of a botnet. Compounding the problem is the millions of Internet of Things (IoT) devices on the open web. They function like simple computers — but are connected to the Internet with little-to-no security, making them easy targets to become zombies or bots. These result in botnets with tremendous amounts of bandwidth that can instantly render unprotected servers offline.
Through a botnet, an attacker can launch DDoS attacks on a victim server by commanding all the zombies or bots in the network to send traffic to the IP address of the victim server at the same time, often over a sustained period. Because these zombies or bots tend to be legitimate machines, it is usually difficult to distinguish botnet controlled traffic from legitimate Internet traffic. DDoS attacks can be carried out at different layers of the seven-layer Open Systems Interconnection (OS) model, depending on the type of the attack. Some of the more common attacks include:
Sophisticated DDoS attacks do not merely attack a single layer, but combine attacks on multiple layers.
Broadly, DDoS attacks can be classified into three main categories: volumetric, protocol, and application attacks.
Volumetric Attacks: The goal of volumetric attacks is to exhaust the bandwidth between a web server and the Internet . When all the bandwidth between a web server and the Internet is exhausted by a malicious volumetric attack, there is no more available bandwidth for legitimate traffic. DNS amplification attacks are one of the most common forms of volumetric attacks. An attacker spoofs the IP address of the victim’s server to query a DNS server using a zombie machine. The DNS servers will then send the responses to the IP address of the victim’s server even though the victim’s server did not actually make a request. An analogy would be someone calling a real estate agency asking for a list of all the available room rentals in your city and to call back to your number with the information. With little effort, that person would have sent your phone with lots of information that you did not request. By commanding a botnet, an attacker can massively amplify the DNS queries, flooding the victim’s server with large amounts of unwanted DNS responses, saturating the bandwidth between the web server and the Internet.
Protocol Attacks: Protocol attacks typically target layers 3 and 4. For example, a SYN flood attack exploits the three-way handshake process needed to establish a transmission control protocol (TCP) connection. Zombie machines initiate the handshake process by sending a SYN packet. However, the zombie machines do not continue to complete the handshake process, leaving the ports occupied and unable to process legitimate requests, thereby crippling the server. In a UDP flood attack, zombie machines send large amounts of UDP datagrams to random ports on the victim server. This causes the web server to look for applications that are currently running and supposed to receive these datagrams on those ports. Because the datagrams are not requested by a running application on the web server, the server will respond with an ICMP packet to inform the sender that the destination was unreachable. With a sufficiently large amount of incoming UDP datagrams, the server will exhaust itself responding with ICMP packets, thus crippling the server.
Application Attacks: For application attacks, they generally operate through sending of HTTP requests. When a client requests for a web page from a web application, the web server often has to execute several scripts and run database queries to fulfill the request. It is much more computationally expensive for a web server to fulfill a HTTP request than it is for a client to make a HTTP request. By controlling a botnet, attackers can easily overwhelm a web server’s computational resource (very) cheaply by flooding a web application on the server with HTTP requests. Basically, HTTP attacks are the equivalent of many users hitting the refresh button on a web browser multiple times -- only that the entire process is automated and remotely performed by attackers through a large network of compromised machines.
DDoS attack mitigation can happen in a few ways: blackhole routing, rate limiting, web application firewalls (WAFs), and Anycast diffusion.
Blackholing IP addresses/null routing: When an address is "blackholed" or "nullrouted," all traffic to a server is pushed through “black hole," never to be seen again. This approach is blunt, as the approach does not distinguish between legitimate or malicious traffic. Although the connection flood is mitigated, the server becomes functionally useless as all traffic is dropped (in other words, the "Denial of Service" was successful).
Ratelimiting: In rate limiting, the number of requests that a web server will accept in a given amount of time is restricted. This prevents a web server from being overwhelmed by a flood of connection requests. Rate limiting is an effective strategy for some forms of DDoS attacks, but it is insufficient for sophisticated DDoS attacks.
Web Application Firewalls (WAF): For layer 7 application attacks, WAFs can help to monitor traffic and filter out malicious traffic, sending only legitimate traffic to a server. This prevents the server from being overwhelmed by DDoS attacks that target this layer.
Anycast Diffusion: This approach makes use of an Anycast network to spread and thin out the large volume of traffic from a DDoS attack across an entire network, effectively absorbing the attack. As an analogy, a DDoS attack is like a heavily-swollen river. By creating multiple canals along the river to divert the river’s water away to be absorbed by other areas, the amount of water in all areas becomes much more manageable, reducing the damage from massive flooding in a small area.
A Distributed Denial of Service attack is a category of attacks that target multiple areas on a server.
The layer of the OSI model that handles communication over networks.
The layer of the OSI model that handles traffic between hosts and clients (TCP/UDP).
The layer of the OSI model that supports applications and web-pages.